Cybersecurity and data protection are overwhelming topics, even for those who have years of experience in technically-oriented subjects. It is, thus, not a surprise to see people shut off when discussions about cybersecurity come to the fore.
This situation, however, is not conducive, especially due to the recent onslaught by malicious entities on financial institutions across the globe. Cybersecurity-related projects can no longer be put on the backburner. It is a topic that everyone ought to understand, even if its only at an elementary level.
To that end, we have boiled down the problem of security to its core, through the use of a framework that anyone can understand, whether it be a C-level executive or someone who is just taking their first steps in the world of security.
Duties Pertaining to Data
According to the United Nations, all stakeholders in the financial services industry have two important duties pertaining to data: privacy and protection – for which it has additional principles.
Privacy really builds on two concepts: ownership (who should own the data and make decisions for its use) and minimalism (an entity should capture or store only that data needed to provide a product or service). These topics, even though of utmost importance and worthy of deep discussion, will not be the focus of this article. (Fintech Cadence has extensively discussed this topic in its open banking paper, which you can read here.)
Data protection, on the other hand, is more about protecting data that you already have and proactively improving these processes to stay current with changing technologies. To do so, one needs to have a high-level understanding of the state of the industry and where it is headed – which will be the topic of the following section.
Trends in Cybersecurity
Even though there are numerous forces shaping the future of Cybersecurity across all levels, three trends are more important than all others, especially for a strategist making decisions on how to best protect their organization’s assets.
1. Numerous verticals and growing
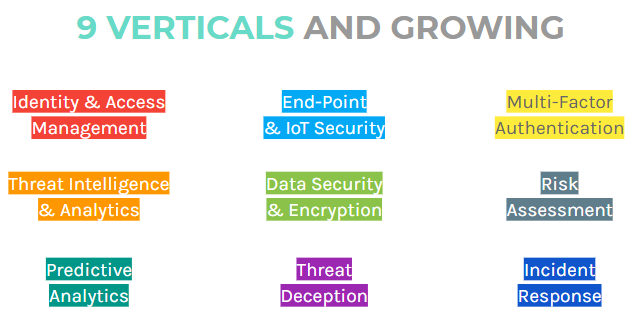
As of now, there are nine verticals in the cybersecurity space. On top of that, these verticals can be overlapping. For instance, three-factor authentication can be part of KYC/identity management, as well as end-point and IoT security.
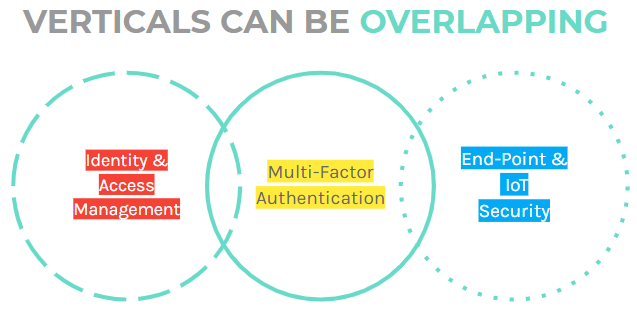
Unless you have a well-defined problem and a clear understanding of the value proposition of each solution, choosing a product can be a daunting task. In most cases, organizations play a game of “patch work,” where they use one product to fix a problem and another to fix something else. The worst part is that most of these products or services are not capable of “communicating” with each other. A situation that is counter to creating a consolidated network of systems (more on this later).
2. Added layers of complexity
The use of third-party vendors and technologies, like IoT and cloud, are making things more complex.
2.1 Internet of Things (IoT): IoT is gaining huge amounts of traction in the fintech sphere. These devices add convenience to the user’s life, and in turn allow corporations to collect data to analyze patterns. Patterns that can be used to build products that provide further convenience to the user. The use of telematics to improve driver safety and inculcate better habits is one such example. The bad news, however, is that IoT also represents the weakest link in the cybersecurity ecosystem for any organization.
A simple example of an IoT attack is through endpoints, where the hacker goes for well-known edge devices that have factory set default passwords or PINs. In this case, the hack is as simple as pulling out the battery and resetting the device. Researchers from Israel’s Ben-Gurion University of the Negreb conducted an experiment where they were able to hack numerous IoT home devices in less than 30 minutes.
The bigger worry is that only about 48 percent of companies are confident they can detect an IoT security breach. i.e. by the time a firm realizes that it has been hacked, the damage would have already been done.
2.2 Cloud: Cloud computing is here to stay, It provides cost cutting and a simple way to move away from legacy systems to most organizations. Gartner predicts the worldwide public cloud service market will grow from $182.4B in 2018 to $331.2B in 2022, attaining a compound annual growth rate (CAGR) of 12.6%.
Cloud computing can come across as risky or safe depending on who you talk to. Corporations that use cloud services provided by organizations such as Amazon which has a suit of security and monitoring tools would likely be content with the level of security provided by Amazon’s comprehensive suite of security and monitoring tools.
Tools that are highly important because just like any organization, the cloud organization is also vulnerable to Distributed-Denial-of-Service Attacks, employee negligence, data loss/damage due to inadequate backup, social engineering etc. Further to this, when an organization uses cloud services, it is trusting a 3rd party to do a stellar job at protecting all the data.
As the astute reader might have surmised by now, moving to the cloud also implies loss of control and visibility. Thus, if a cloud service that does not provide adequate visibility and security tools, it would be deemed insecure. Dropbox for instance has been under constant criticism for not following proper security measures.
So as long as there are cloud providers not spending enormous amounts of money to have the best security protocols and clients who use these services, the cloud as a whole is likely to have the reputation of an unsafe environment.
2.3 Application Program Interface (API) : According to a study done by McKinsey, as much as $1 trillion in total economic profit globally could be up for grabs through the redistribution of revenues across sectors within ecosystems. In colloquial terms: a lot of money is to be made through the use of APIs. So it’s safe to assume that APIs will become more and more ubiquitous in the coming years.
Like every new technology, though, APIs come with their own set of risks. Risks that even organizations with the deepest pockets cannot mitigate – as evidenced by attacks on Google, Apple and Facebook.
Even communication between mobile applications and APIs that takes place through the gold standard of internet encryption, HTTPS, can easily be intercepted and read. Tools to do this are not top secret, in fact, they are easily downloadable on the Google Play store. Through this application called Packed Capture, one can not only decrypt communication, but also discover sensitive and supposedly confidential information like API keys and OAuth tokens.
3. Sophisticated Attacks
Malicious entities, like cancer cells, will adapt and continue to harm the host. The use of AI/ML for cybersecurity is quite difficult because AI works well when it recognizes patterns, which are hard in the case of cybersecurity, as every attack is so different.
But let’s assume, for the purpose of a thought experiment, that AI is able to create a sophisticated security system. In this scenario, an organization’s AI system would protect against an attack. But a malicious entity would use AI to recognize patterns the organization’s AI is using and orchestrate an attack to defeat the host’s AI. This will go on as a loop, ultimately creating a vicious circle.
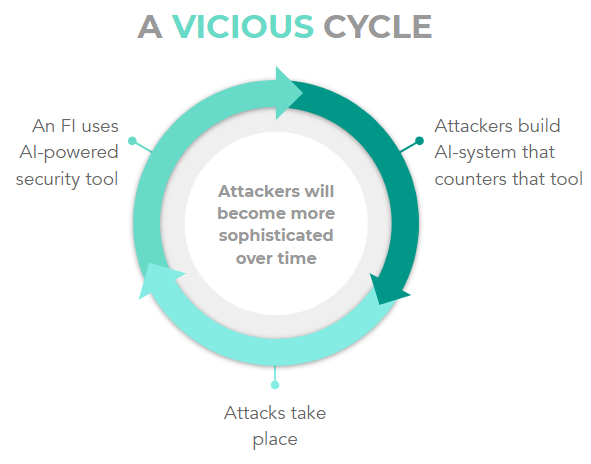
At this point you might be wondering if the attackers will have the financial resources to conduct such sophisticated attacks.
Attacks as of now are quite sophisticated and resource-intensive. When hackers stole Oauth tokens in October 2014, they impersonated thousands of Twitter and Facebook users, phish attacked two seperate companies, penetrated and screen scrapped a customer support application and made thousands of unauthorized Twitter and Facebook posts.
Furthermore, the size of the cybercrime market is huge. And as long as there is money to be made, there will be malicious entities looking to hack into a system. Below are some statistics that paint the picture.
-
Cybercrime is relatively far more profitable versus the combined operations of drug trafficking worldwide. (Cisco)
-
Over 70% of the global cryptocurrency market will be used in criminal activities. (Cybersecurity Ventures)
-
The FBI’s Cyber’s Most Wanted List includes 63 notorious criminals known to have committed a string of cybercrimes that have endangered and cost people and organizations billions of dollars. (FBI)
-
Only 10% to 12% of the actual number of committed cybercrimes are reported to authorities. (Slate)
-
Businesses operating in the Asia-Pacific region receive 6 cyber threats every minute. (Cisco)
The bottomline is that cyberspace is a lucrative space for malicious entities and they will continue with attacks in the coming years.
The Data Lifecycle
Every bit of data goes through this process, whether it be data on Google sheets or confidential client information on the cloud. Developing a mindset based on this lifecycle alone can allow better communication between business and IT teams, in addition to asking the right questions when embarking on the next tech project within the bank.
The data process below is presented in a linear fashion, but that’s not necessarily always the case. It could be that the act of storage takes place both before and after transfer. And if the data leaves the organization for processing, all the steps are repeated, under the third party’s data lifecycle.
What does all this really mean for security?
At the most elementary level, one should ask the following questions at each stage:
-
Transfer/capture: are my end points, all the way from websites/apps to PoS payment systems, secure?
-
Storage: where is the data stored and who would have access to it in the physical and virtual world?
-
Transfer: is the data that is being transferred within and outside the organization done in an encrypted process, especially when it comes to sensitive personal data?
Processing: have all third-party vendors been properly vetted? Are they using APIs that have the right response-mechanisms in case of an attack?
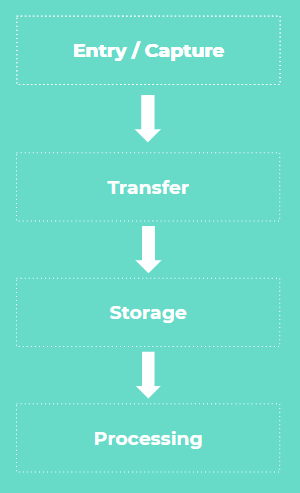
For an organization with thousands of employees and multiple divisions, each of these big steps in the process will have smaller associated processes, which at a bird’s eye view will look like a spiderweb.
And as a rule of thumb, the more processes an organization has, the more vulnerable it is to attacks.
The big takeaway, thus, is to consolidate and streamline your IT infrastructure as much as possible. If an organization has to deal with multiple vendors, systems should be able to communicate with each other in an easy fashion. If there are too many redundancies, they should be eliminated. But the bottom-line should always be: consolidate and monitor


